Typically, the work done at Bletchley Park receives most of the glory for breaking Enigma. But the complete story actually begins in Warsaw, Poland in 1919. Of all codebreakers, the Polish Cipher Bureau, spearheaded by Marian Rejewski, did the first codebreaking. This is a largely untold story that suggests that without Rejewski’s codebreaking groundwork, Alan Turing would have had to start from scratch.
I. The Birth of an Enigma in Germany
Arthur Scherbius was a born electrical engineer, and businessman. His father was in business, and Arthur himself studied electricity at the Technical University Munich, and later the University of Hanover. He was awarded a doctorate in engineering in 1904, after his “Proposal for the Construction of an Indirect Water Turbine Governor” dissertation. So it was only logical that he would go on to found his own firm, Scherbius & Ritter, and patent a number of inventions for commercial use – ceramic heating parts, electric pillows, asynchronous motors for which his name became synonymous… and a cipher machine.
Scherbius and his partner Ritter had a patent filed for their cipher machine on the 23rd of February, 1918. The machine was based on rotating wired wheels, now known as a rotor machine. Arthur was looking for a corner on that market, and purchased yet another patent for a rotor machine the following year.
Unfortunately, business was slow. The two originally tried to pitch their product to the German Navy, but were turned down. The invention was given new life under Gewerkschaft Securitas, who founded the Cipher Machines Stock Corporation in July 1923, giving Scherbius and Ritter seats on the board of directors. They called their commercial product Enigma.
 Various Enigma Versions, by Hohum @ Wikimedia.
Various Enigma Versions, by Hohum @ Wikimedia.
Enigma began life on exhibition at the Congress of the International Postal Union in 1923. This Model A was a bulky machine – complete with a typewriter – weighing over 100 pounds. In 1924, model B came out, an 8-rotor printing sibling. A year later, Enigma C came along, which really revolutionized the development of the line. It was affectionately nicknamed the “glowlamp Enigma”, having done away with the typewriter by relying entirely on the operator, in favor of portability. It was also the first Enigma to include a reflector, which takes the input and reflects back the electrical signal for its return journey through the rotors. There are two possible reflectors, each of which is wired up differently so that the input letter is transformed to a different letter when reflected back.
The legacy was clinched however with Enigma D, with shipments to Sweden, the Netherlands, United Kingdom, Japan, Italy, Spain, United States and Poland. With the rest of the world catching up on the military and diplomatic uses of Enigma, the German Navy recognized the error of their ways. Funkschlüssel C, or Radio cipher C, was introduced into service in 1926. It had 29 letters, allowing X to go through unencrypted. The German Army caught on to the latest fad in 1928 with Enigma G, their own exclusive version of Enigma.
The Enigma G was then modified to Enigma I, or the Wehrmacht Enigma, largely in use by German services and government before and during World War II. The major difference between these kinds of military models and the commercial models was the addition of a plugboard to swap pairs of letters, which greatly increased its cryptographic strength. You’ll remember, military models also benefited from the edition of reflectors, and a massive weight loss for portability – 26 pounds, as compared to the previous 110.
By 1934, the army version of the Enigma had spread to the Air Force and the Navy, with the benefits of increased security from the plugboard and easier inter-service communications with the standardization across branches. Thus the Navy introduced the M3 into service. The Navy version was modified to give a choice of three rotors out of a possible five, whereas the army version only had three rotors.
The machine used a plugboard to swap pairs of letters, and the encipherment varied from one key press to the next. For two operators to communicate, both Enigma machines had to be set up in the same way. The large number of possibilities for setting the rotors and the plugboard combined to form an astronomical number of configurations, and the settings were changed daily, so the machine code had to be “broken” anew each day.
Arthur Scherbius, the father of Enigma if you will, died in 1929 during a horse carriage accident. He did not get to experience the standardization of his invention, nor the travesties that it was responsible for prolonging.
II. The Polish drop the Bomba
It was only May 1919 when the Polish began the precursor to the Cipher Bureau. Perhaps they had an inkling of things to come, after just having witnessed the Great War. The purpose of the Bureau was to create “bomba”, or a cryptologic bomb to break Enigma, after French intelligence acquired operation manuals and sample messages for the German Enigma cipher machine. French intelligence officer Captain Gustave Bertrand supplied this material to Poland’s Cipher Bureau, which used it as part of their successful effort to break Enigma.
Marian Rejewski designed bomba. He was a mathematician and cryptologist, trained at Poznan University. One fateful day, he was invited to attend a secret cryptology course, taught by the Cipher Bureau. The head of the Cipher Bureau’s German section, Captain Maksymilian Ciężki, tasked Rejewski to work alone on the German Enigma I machine for a couple hours per day; Rejewski was not to tell even his colleagues what he was doing.
He joined the organization in September 1932. To date, the Bureau had had little success with reading Enigma-encrypted messages intercepted from the Germans. However, that was about to change with Rejewski’s help…
After only a few weeks working for the Bureau, Rejewski was able to deduce the inner-wiring of Enigma. With his two assistants, Rejewski then was able to start working on methods for regular decryption, eventually reconstructing the Enigma cipher machine sight-unseen. These techniques were put to use in designing the bomba in 1938. Six of these machines were constructed for each possible rotor pattern. Each bomba conducted an exhaustive analysis of the 17,576 possible message keys. This automated process took the place of about one hundred workers and shortened the time for obtaining a key to about two hours.
In December 1938, the German Army increased the complexity of Enigma by adding two additional rotors. This increased the number of possible wheel orders from 6 to 60. The Poles did not have the resources to commission 54 more bombs. Other Enigma users received the two new rotors at the same time, but the intelligence agency of the SS and the Nazi Party continued to use its machines in the old way until July 1939. This allowed Rejewski to reuse his previous method, and he had worked out the wirings of the two new rotors by the end of the year. However, on the 1st of January 1939, the Germans increased the number of plugboard connections from between five and eight to between seven and ten, which made decryption even more difficult.
III. Warsaw: A meeting to change History
It’s late July during the summer of 1939, and war is potent in the air. The scent hung especially thickly above Warsaw, even five weeks before the German invasion of the country or the British declaration of war. The Polish Cipher Bureau was not waiting on the British – they called the French and British military intelligence teams to Warsaw to share all of their results. Both countries were expanding their decryption efforts in anticipation of war, and this continued after the war started.
The Warsaw Meeting was designed to share the Bureau’s Enigma-decryption techniques and equipment to the representatives sent over by the French and British, as they had not yet been able to make much progress in the struggle to crack Enigma. It was Marian Rejewski and his colleagues who presented their findings to the assembled representatives that day. Their presentation, code-named Ultra, included Zygalski sheets, the cryptologic bomb, and the promise of a reconstructed Enigma for each delegation. This intelligence transfer would change the course of the war in providing the Allies with the Ultra technology, and eventual victory.
IV. Bletchley Park takes the Enigma torch
Alan Turing had been working part-time with the government code and cipher school since September 1938. He and Dilly Knox, a senior codebreaker, focused on cryptanalysis of the Enigma. Codebreaking operations moved from London to a country house near the railroad in Bletchley Park once Britain declared war on Germany on the 3rd of September 1939.
Soon after the July 1939 Warsaw meeting, Turing and Knox began work on a less fragile approach to the problem. The Polish method relied on an insecure indicator procedure that the Germans were likely to change, and did so in May 1940. Turing’s approach was more general, using crib-based decryption for which he produced the functional specification of the bombe, which was an improvement of the Polish Bomba.
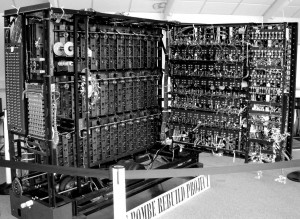 Recreation of the British Bombe.
Recreation of the British Bombe.
The bombe was the first of five major cryptanalytical advances that Turing made during the war. The others were: deducing the indicator procedure used by the German navy, developing a statistical procedure for making more efficient use of the bombes, developing a procedure for working out the cam settings of the wheels of the Lorenz SZ 40/42 dubbed Turingery, and the development of a portable secure voice scrambler at Hanslope Park that was code-named Delilah. It has been estimated that this work shortened the war in Europe by as many as two to four years
By using statistical techniques to optimize the trial of different possibilities inthe code breaking process, Turing made an innovative contribution to the subject. He wrote two papers discussing mathematical approaches, entitled The Applications of Probability to Cryptography and Paper on Statistics of Repetitions. These papers were of such value to GC&CS that they were not released to the UK National Archives until April 2012.
V. PC Bruno: the Polish on the Lam
After the outbreak of war the Polish cryptologists were soon relocated to continue operations in France. During that time they stayed at PC Bruno, the Polish-French signals intelligence station near Paris. PC Bruno worked in close cooperation with Britain’s decryption operations at Bletchley Park. The Polish group was led by Lt. Col. Gwido Langer, and included the mathematicians who been breaking Enigma for seven years already, Marian Rejewski, Jerzy Różycki, and Henryk Zygalski. In the interest of security, Bletchley Park and PC Bruno corresponded using the supposedly unbreakable Enigma.
They stayed at PC Bruno until the fall of France in 1940. As German forces were approaching PC Bruno, Gustave Bertrand evacuated the Bruno staff just after midnight on June 10th. Bertrand was a French military intelligence officer. France surrendered on the 22nd of June. Two days later. Bertrand flew the staff in three planes to Algeria. In September 1940, Bertrand secretly returned them to France. He established a new decryption center at Uzès on the Mediterranean coast, in the unoccupied “Free Zone” of France. This center, codenamed Cadix, resumed breaking ciphers until the German occupation of southern France in November 1942. At that time, all staff was forced to evacuate again, assuming work undercover in Vichy France.
As late as December 1939, when Lt. Col. Langer and French Air Force Capt. Henri Braquenié visited London and Bletchley Park, the British asked that the Polish cryptologists be made available to them in Britain.
There, they were inducted into the Polish Army and put to work breaking German SS and SD hand ciphers at a Polish signals facility in Boxmoor. Due to their having been in occupied France, it was thought too risky to invite them to work at Bletchley Park.
 Bletchley Park by Magnus Manske @ Wikimedia.
Bletchley Park by Magnus Manske @ Wikimedia.
VI. RIP Enigma
Cryptanalysis of the Enigma enabled the western Allies in World War II to read substantial amounts of secret Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the code-name Ultra. This was considered by western Supreme Allied Commander Dwight D. Eisenhower to have been “decisive” to the Allied victory.
The Enigma machines produced a polyalphabetic substitution cipher. During World War I, inventors in several countries realized that a purely random key sequence, containing no repetitive pattern, would, in principle, make a polyalphabetic substitution cipher unbreakable.
Decrypting enciphered messages involves three stages, defined somewhat differently in that era than in modern cryptography. First, there is the identification of the system in use, in this case Enigma; second, breaking the system by establishing exactly how encryption takes place, and third, setting, which involves finding the way that the machine was set up for an individual message, i.e. the message key. Today, it is often assumed that an attacker knows how the encipherment process works and breaking specifically refers to finding a way to infer a particular key or message. Enigma machines, however, had so many potential internal wiring states that reconstructing the machine, independent of particular settings, was a very difficult task.
A major weakness of the system, however, was that no letter could be enciphered to itself. This meant that some possible solutions could quickly be eliminated because of the same letter appearing in the same place in both the ciphertext and the plaintext.
For an enemy to decipher German military Enigma messages required that the following were known:
Unchanging structure of the machine
- The wiring between the keyboard (and lampboard) and the entry plate.
- The wiring of each rotor.
- The number and position(s) of turnover notches on the rings of the rotors.
- The wiring of the reflectors.
- Internal settings (usually changed less frequently than external settings)
Changing Variables
- The selection of rotors in use and their ordering on the spindle.
- The positions of the alphabet ring in relation to the core of each rotor in use
- External settings (usually changed more frequently than internal settings)
- The plugboard connections.
- The rotor positions at the start of enciphering the text of the message.
 Navy Enigma at the National Cryptologic Museum.
Navy Enigma at the National Cryptologic Museum.
The strength of the security of the ciphers produced by the Enigma machine was due to the large numbers associated with the scrambling process. It produced a polyalphabetic substitution cipher with a period (16,900) that was many times the length of the longest message. The 3-rotor scrambler could be set in 26 × 26 × 26 = 17,576 ways, and the 4-rotor scrambler in 26 × 17,576 = 456,976 ways. With six leads on the plugboard, the number of ways that pairs of letters could be interchanged was 100,391,791,500 (100 billion) and with ten leads, it was 150,738,274,937,250 (150 trillion).
However, the way that Enigma was used by the Germans meant that, if the settings for one day (or whatever period was represented by each row of the setting sheet) were established, the rest of the messages for that network on that day could quickly be deciphered.
The security of Enigma ciphers did have fundamental weaknesses that proved helpful to cryptanalysts. A letter could never be encrypted to itself, a consequence of the reflector. This property was of great help in using short section of plaintext (referred to as a crib) thought to be somewhere in the ciphertext—and could be used to eliminate a short section of plaintext in a particular position. For a possible location, if any letter in the crib matched a letter in the ciphertext at the same position, the location could be ruled out. It was this feature that Alan Turing exploited in designing the British bombe.
Further, the plugboard connections were reciprocal, so that if A was plugged to N, then N likewise became A. It was this property that led mathematician Gordon Welchman at Bletchley Park to propose that a diagonal board be introduced into the bombe, substantially reducing the number of incorrect rotor settings that the bombes found. The notches in the alphabet rings of rotors I to V were in different positions, which helped cryptanalysts to work out the wheel order by observing when the middle rotor was turned over by the right-hand rotor.
Identical setting of the machines at the transmitting and receiving ends was achieved by key setting procedures. These varied from time to time and across different networks. They consisted of setting sheets in a codebook, which were distributed to all users of a network, and were changed regularly. The message key was transmitted in as part of the message preamble. The word key was also used at Bletchley Park to describe the network that used the same Enigma setting sheets. During World War II the settings for most networks lasted for 24 hours. The sheets had columns specifying, for each day of the month, the rotors to be used and their positions, the ring positions and the plugboard connections. For security, the dates were in reverse chronological order down the page, so that each row could be cut off and destroyed when its cycle was completed.
Up until the 15th of September 1938, the transmitting operator indicated to the receiving operator how to set their rotors, by choosing the three-letter key specific to that message, and enciphering it twice using the specified initial ring positions. The resulting 6-letter indicator, was then transmitted before the enciphered text of the message.
The weakness in this indicator procedure came from two factors: First, use of a global key —this was changed in September 1938 so that the operator selected his initial position to encrypt the message key, and sent the initial position in clear followed by the enciphered message key; The second problem was the repetition of message key within the indicator. The message setting was encoded twice, resulting in a relation between first and fourth, second and fifth, and third and sixth character. This security problem enabled the Polish Cipher Bureau to break into the pre-war Enigma system as early as 1932. On 1 May 1940 the Germans changed the procedures to encipher the message key only once.
The system’s greatest weakness was the way that it was used. The basic principle of this sort of enciphering machine is that it should deliver a very long stream of transformations that are difficult for a cryptanalyst to predict. Some of the instructions to operators, however, and their sloppy habits, had the opposite effect. Without these operating shortcomings, Enigma would, almost certainly, not have been broken.
VII. Fatal Flaws
While the Enigma was one of the best encryption devices of its time, there were a few fatal flaws in its design and use.
1. Design error – A letter would never be encrypted to itself.
2. Design error – A one-to-one relationship of characters.
3. User error – Predictable preamble patterns.
4. User error – Predictable sign-off patterns.
5. User error – Predictable phrase patterns.
Thus, the greatest German flaw was to follow predictable patterns. The most important lesson here is to never reduce your own workload through the use of any type of pattern, in the interest of security.